The ICS-SEC KG is a cybersecurity knowledge graph that integrates and links critical cybersecurity information of Industrial Control System (ICS) and Operational Technology (OT) from various publicly available sources. It extends the existing SEPSES-CSKG by including ICS-related security resource such as Industrial Control System Advisory (ICSA) and MITRE ATT&CK for ICS. The Knowledge Graph is continuously updated to reflect the dynamic changes in ICS-Security landscape.
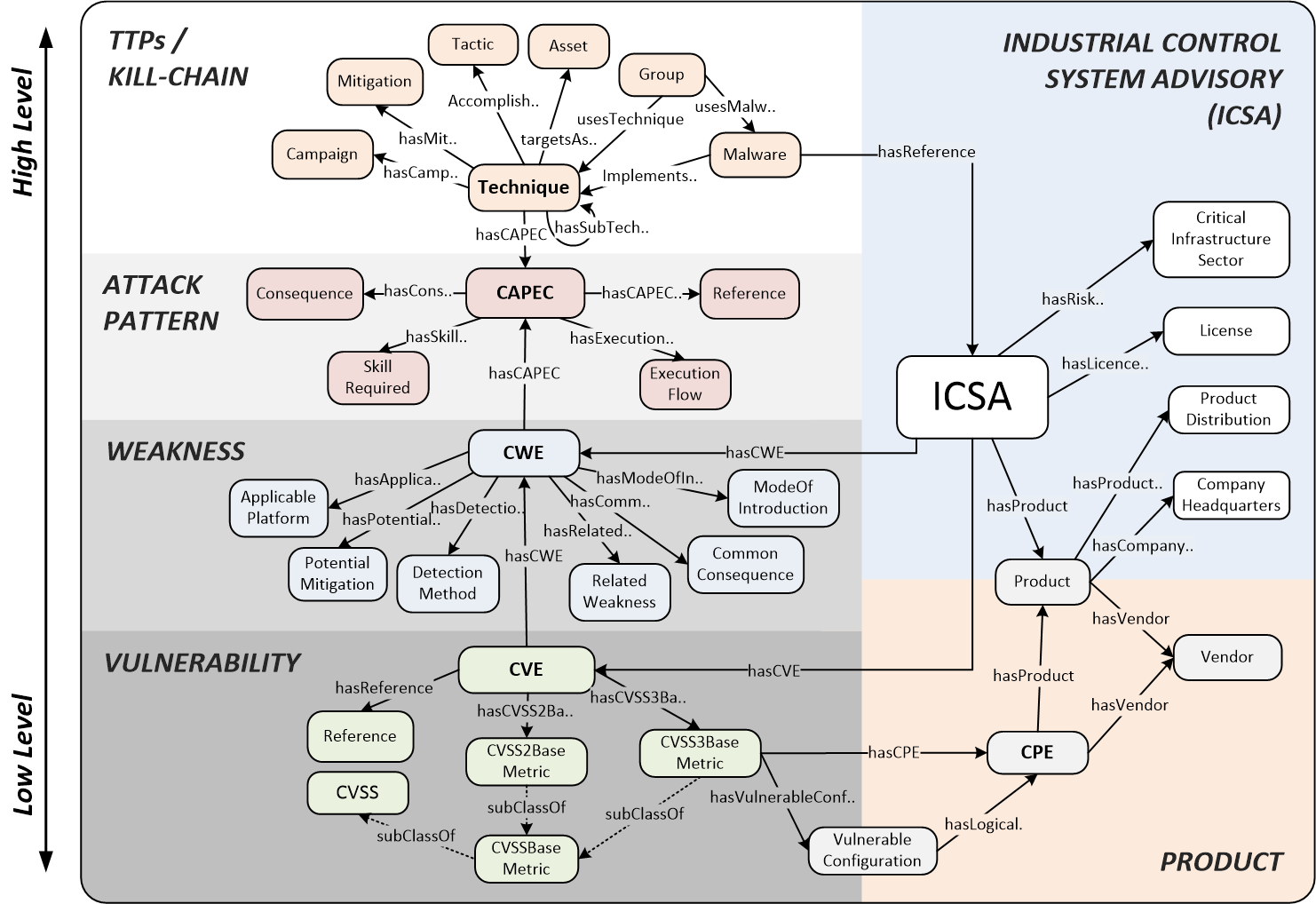
The ICS-SEC ontology is depicted in the following figure:
Figure 1: Integrated ICS-SEC Ontology.
The integrated ICS-SEC ontology can be found here. It consists of seven RDF/OWL-based vocabularies:
| Prefix | Description | Namespace and Documentation (click at the link!) |
|---|---|---|
| attack | MITRE ATT&CK / ATT&CK for ICS | http://w3id.org/sepses/vocab/ref/attack |
| icsa | Industrial Control System (ICS) Advisory | http://w3id.org/sepses/vocab/ref/icsa |
| capec | Common Attack Pattern Enumeration and Classification (CAPEC) | http://w3id.org/sepses/vocab/ref/capec |
| cwe | Common Weakness Enumeration (CWE) | http://w3id.org/sepses/vocab/ref/cwe |
| cve | Common Vulnerabilities and Exposures (CVE) | http://w3id.org/sepses/vocab/ref/cve |
| cvss | Common Vulnerability Scoring System (CVSS) | http://w3id.org/sepses/vocab/ref/cvss |
| cpe | Common Platform Enumeration (CPE) | http://w3id.org/sepses/vocab/ref/cpe |
To query/access the constructed KG, we provide several interfaces:
| Service Type | Description | License | Persistent URL |
|---|---|---|---|
| SPARQL Endpoint | Using SPARQL to query the KG | MIT License | http://w3id.org/sepses/sparql |
| Linked Data Interface | Browsing the linked data through a web page | MIT License | http://w3id.org/sepses/resource/cpe/product/triton (example) |
| Linked Data Fragment-Server | Using LDF-Client to query the KG | MIT License | http://w3id.org/sepses/ldf |
| Dump File | Latest KG dump file in Turtle (.ttl) and HDT (.hdt) format | MIT License | http://w3id.org/sepses/dumps/latest |
This query example ilustrates vulnerability assesment to a certain assets in typical ICS infrastructure namely "Siemens".
PREFIX cvss: <http://w3id.org/sepses/vocab/ref/cvss#>
PREFIX cve: <http://w3id.org/sepses/vocab/ref/cve#>
PREFIX SOAR4IoT: <http://w3id.org/sepses/vocab/SOAR4IoT#>
PREFIX icsa: <http://w3id.org/sepses/vocab/ref/icsa#>
SELECT distinct ?cveId ?cvssScore ?icsaId ?cweId
WHERE { ?s a <http://w3id.org/sepses/vocab/SOAR4IoT#policy> .
?s SOAR4IoT:hasCPE ?cpe .
?cveId cve:hasCPE ?cpe .
?cveId cve:hasCVSS3BaseMetric ?cvss .
?cvss cvss:baseScore ?cvssScore.
?icsaId icsa:hasCVE ?cveId .
?icsaId icsa:hasCWE ?cweId
FILTER(regex(STR(?s),"Siemens"))
}
ORDER by DESC(?s)
LIMIT 5other example queries can be found here.
- Open the ICS-SEC query editor through SPARQL Endpoint or LDF-Client query service.
- Copy the SPARQL query above (or pick another example) and paste it to the query editor.
- Run the Query.
- To explore the KG further via Linked Data Interface, just follow the link of an entity, for example http://w3id.org/sepses/resource/icsa/ICSA-19-283-01.
To guarantee the quality and consistency of the constructed knowledge graph, ICS-SEC leveraged a declarative RDF Mapping (i.e., RML) and used SHACL to validate them. The following snippets depicts an example of RML mapping for ICSA resource from JSON file and its SHACL rule.
..
<#SubjectMapping> a rr:TriplesMap ;
rml:logicalSource [
rml:source [
a carml:Stream ;
] ;
rml:referenceFormulation ql:JSONPath ;
rml:iterator "$"
] ;
rr:subjectMap [
rr:template "http://w3id.org/sepses/resource/icsa/{document.tracking.id}" ;
] ;
rr:predicateObjectMap [
rr:predicate rdf:type;
rr:objectMap [ rr:template "http://w3id.org/sepses/vocab/ref/icsa#ICSA" ];
];
rr:predicateObjectMap [
rr:predicate dcterm:identifier;
rr:objectMap [ rml:reference "document.tracking.id" ];
rr:datatype rdfs:Literal ;
];
...The complete RML mapping be found here.
...
ssr:icsaValidator
a sh:NodeShape ;
sh:closed true ;
sh:name "ICSA Class validation" ;
sh:description "ICSA Class validation" ;
sh:property [ sh:maxCount 1 ;
sh:minCount 1 ;
sh:path rdf:type
] ;
sh:property [ sh:maxCount 1 ;
sh:minCount 1 ;
sh:path dcterm:identifier
] ;
sh:property [ sh:maxCount 1 ;
sh:minCount 1 ;
sh:path dcterm:title
] ;
sh:property [ sh:maxCount 1 ;
sh:minCount 1 ;
sh:path capec:issued
] ;
sh:property [ sh:minCount 1 ;
sh:path icsa:hasCVE ;
sh:dataType cve:CVE
] ;
sh:property [ sh:minCount 1 ;
sh:path icsa:hasProduct ;
sh:dataType cpe:Product
] ;
sh:targetClass icsa:ICSA
...The complete SHACL rule be found here.
To run this prototype, the prerequisite is that you have a JDK 8+ and Maven installed in your computer.
Additionally, the config.properties is build for local Jena fuseki installation. Make sure that:
- the
config.propertiesis available (and adjust it if necessary; especially with regards to the triplestore/fuseki installation) - you have an empty repo called 'sepses' in your fuseki/virtuoso installation
- you can also run it without storing the data to triplestore using "dummy" as storage
- currently still need an active sparql endpoint (TODO: to fix this).
The following steps are required to run the engine:
- run
mvn cleanto build the required jar files from thelibfolder - run
mvn install -DskipTests=trueto build the application- optionally, you can also run the tests (without the
-DskipTests=true) to run checks of extracted data against a set of SHACL constraints to make sure that the conversion for each source is correctly defined
- optionally, you can also run the tests (without the
- run
java -jar target/cyber-kb-<version>-jar-with-dependencies.jar -p <type-of-source>- replace
<type-of-source>with one of the following: capec, cwe, cve, cat, icsa ) - replace
<version>with the version of the Cyber-KB - (optional) you can also add
-vas parameter to activate SHACL constraint checking- Note: this option may add a significant time to the process (especially for CPE)
- replace
The prototype will then
- (i) generate the RDF graph from these sources and create necessary linking
- (ii) (optional) check the generated RDF data against a set of SHACL constraints (using constraints from
src/main/resources/shacl/*.ttl) - (iii) store the data in the triplestore
We have tried and tested it in OSX (Intel i7@3,1GHz, OSX Mojave, 16GB RAM). The benchmark result (excluding SHACL check) is available in the following link.
The ICS-SEC KG is written by SEPSES team and released under the MIT license.